IoT Cryptography: Safeguarding the Connected World

The Internet of Things, or IoT, continues to shape ultramodern life by connecting bias across homes, industries, and healthcare. Many people still question whether IoT security can truly protect sensitive data. To ease these concerns, experts highlight the importance of cryptography in IoT, as it secures communication and builds trust in digital systems. Additionally, understanding […]
Machine Learning Infrastructure: Foundation for Smarter AI
In the moment’s digital frugality, infrastructure for machine learning plays a central part in driving invention across intelligence. Organizations worldwide are redefining how to implement systems, manage resources, and ensure scalability for ultramodern workloads. As artificial intelligence continues to form, the demand for proficient professionals and effective fabrics continues to grow steadily. Also, businesses no […]
Infrastructure as Code Platforms: Simplifying IT Management
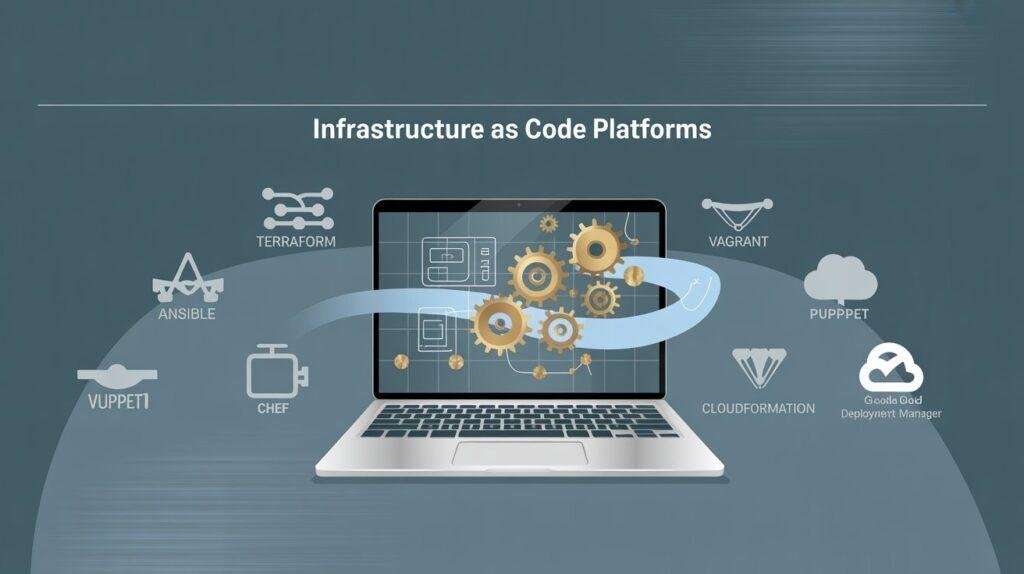
Technology is evolving rapidly, and associations need dependable ways to manage complex systems. Infrastructure as Code platforms offer that trustworthiness. They help teams replace homemade setups with automated, harmonious environments. This shift reduces errors and saves time. Importantly, it also helps businesses scale quickly. Through automation, these platforms allow inventors to concentrate on invention rather […]
Infrastructure as Code: A Complete Professional Guide
The way IT is structured has changed a lot in recent times. In the story, brigades had to configure waiters manually. This was slow, repetitious, and prone to crime. With business needs growing rapidly, companies started looking for quicker and smarter styles. That’s where infrastructure-as-code has come, the ultramodern approach. This article offers infrastructure as […]
Converged Infrastructure: A Complete Guide

In the current rapid digital landscape, companies are always looking for methods to streamline their IT processes while enhancing efficiency. This is where converged infrastructure becomes relevant. A converged infrastructure combines servers, storehouse, and networking into one optimized system rather than handling them singly. This integration streamlines operations, reduces costs, and improves the effectiveness of […]
Quantum Qubit: What is a Qubit?
Quantum computing is progressing fleetly. It provides advanced results for wisdom, technology, and assiduity, exceeding the capabilities of traditional computing. To truly appreciate this progress, understanding its foundation is pivotal. At the core of this foundation is the quantum qubit. A qubit signifies more than just a technical idea. Instead, it acts as the fundamental […]
MLOps Guide: Best Practices, Tools, and Career Paths

In today’s speedily paced AI-driven landscape, building machine learning models is just the start. Operationalizing them at scale is where the real challenge lies. Drink to the world of MLOps — a practice that merges machine learning with DevOps to streamline ML workflows. This MLOps companion is designed for AI practitioners, inventors, and IT leaders […]
Best MLOps Platforms

What does MLOps stand for? It represents Machine Learning Operations. Machine Learning (ML) is rapidly advancing, and with it comes the necessity to oversee its activities. This is the point at which the best MLOps platforms become relevant. However, before delving into specifics, let’s examine the basis. This field combines concepts from DevOps, data engineering, […]
Define MLOps? Architecture,Use Cases, Tools

Machine Learning Operations, or MLOps, is a core growth area in the field of artificial intelligence. The AI projects’ successes realized in the field prompt the logistics support needs for model deployment and monitoring operations to increase rapidly across sectors. This article depicts some of the important MLOps concepts, such as define MLOps, the architectural […]
Semantic Search AI: How semantic searching works?

In the present digital age, traditional keyword-grounded search methodologies frequently fall short. They fail to understand user intent, contextual meaning, or the connections between notions. This is where semantic searching transforms how we interact with data. With the rise of semantic search AI, users now enjoy more relevant, intuitive, and intelligent results than ever before. […]

