Machine learning is a potent tool, learning from data to make predictions or decisions. Yet, it’s not flawless—malicious inputs, known as adversarial instances, can deceive models, leading to incorrect or harmful outputs. In the ever-evolving landscape of ML, the concept of adversarial robustness for machine learning has emerged as a crucial facet. As artificial intelligence (AI) continues to permeate diverse sectors, understanding and mitigating vulnerabilities becomes paramount.
Hence, this article explores adversarial machine learning attacks, their cross-domain impact, and solutions to fortify adversarial robustness for machine learning. Moreover, it underscores using adversarial training to strengthen machine learning models against changing threats.
Adversarial Machine Learning
Adversarial machine learning aims to protect models from deceptive input changes, improving their reliability in real-world scenarios. Additionally, it focuses on creating defenses to counter such attacks and strengthen machine learning models for practical applications.
Adversarial Machine Learning Examples
To comprehend the significance of adversarial robustness, one must delve into real-world scenarios. Adversarial machine learning examples illustrate instances where malicious actors exploit vulnerabilities in AI models. For example:
- An attacker might add noise to a panda image, tricking the model into classifying it as a gibbon.
- Alternatively, placing a sticker with a specific pattern on a stop sign could make an autonomous vehicle mistake it for a yield sign.
Adversarial Machine Learning Attacks
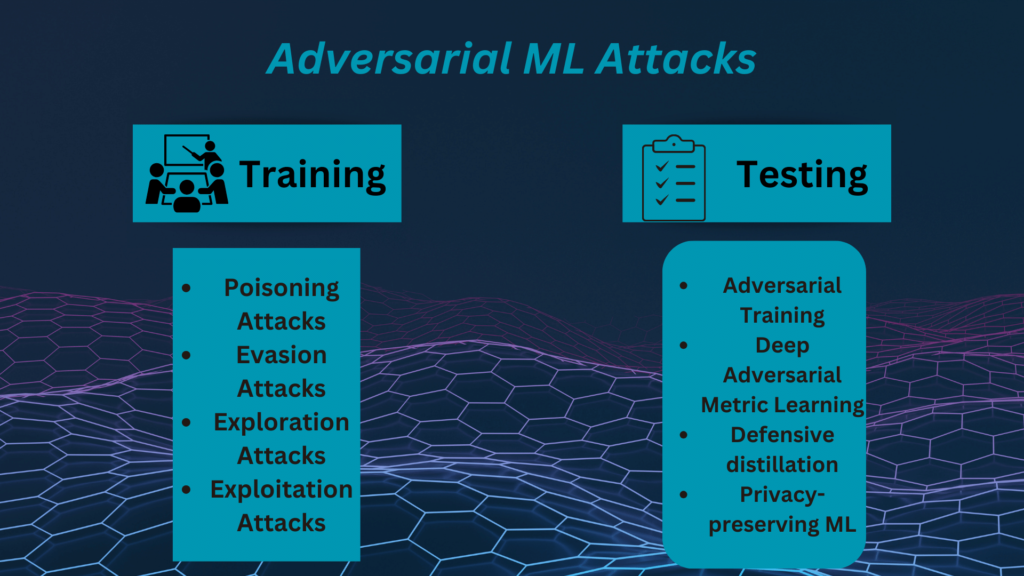
Adversarial machine learning attacks aim to exploit weaknesses in machine learning models. Some common types include:
Poisoning Attacks:
The attacker tampers with the model’s training data to reduce accuracy or introduce bias. For instance, injecting harmful data into a spam filter to misclassify legitimate emails.
Evasion Attacks:
The attacker changes test or input data to avoid detection or induce misclassification. Additionally, Evasion 100, a key concept, involves manipulating data to deceive machine learning models stealthily. Evasion attack examples include subtly altering an image to deceive a face recognition system.
Exploration Attacks:
The hacker investigates the model by asking it questions to extract information and understand how it works. This is similar to a hacker scanning a network to discover open doors and services, aiming to find ways to infiltrate the system.
Exploitation Attacks:
The attacker uses the model’s outputs to gain an advantage or cause harm. For example, manipulating user preferences in a recommender system.
How do Adversarial Machine Learning Attacks Affect Different Domains?
Adverse impacts from machine learning attacks can significantly affect diverse domains that depend on these models. Illustrative instances include:
Adversarial Attacks on Medical Machine Learning
The intersection of machine learning and healthcare introduces critical considerations. For instance, a malicious actor could manipulate medical images or records to deceive machine learning models that assist doctors. Moreover, an attacker could manipulate an image of a benign skin lesion to appear malignant. He canadd a fake tumor to an MRI scan. Additionally, they could tamper with blood pressure readings to deceive healthcare professionals about a patient’s health. Hence, these Adversarial machine learning attacks pose a threat to patient diagnosis, treatment, or prognosis.
Adversarial Machine Learning Cybersecurity
To fortify systems against adversarial threats, a holistic approach to adversarial machine learning cybersecurity is essential. Moreover, it threatens the security of applications like autonomous vehicles, facial recognition, medical imaging, and financial trading. Furthermore, Adversarial machine learning attacks have the potential to circumvent or undermine security systems relying on machine learning models.
For instance, an attacker might employ ARP poisoning attacks to falsify network device IP addresses and intercept traffic. Moreover, an ARP poisoning attack can be active with fake responses diverting traffic, or passive, involving listening to ARP requests.
Quantum Adversarial Machine Learning
Adversarial machine learning attacks can exploit the quantum properties of the data or the model to cause interference. Moreover, it poses a serious threat to the security of quantum applications. Also, it takes advantage of issues like noise and hardware limitations to manipulate or deceive quantum machine learning models. Furthermore, it is crucial for applications like quantum cryptography, quantum metrology, quantum chemistry, etc. Also, An attacker might use quantum adversarial machine learning to create deceptive examples, tricking quantum machine learning models.
Possible Solutions to Improve Adversarial Robustness for Machine Learning
Adversarial Training
To answer the question What is Adversarial Training? machine learning models are equipped to withstand adversarial attacks. This involves exposing models to crafted adversarial examples during training, enabling them to learn robust features. Moreover, the resilience cultivated through adversarial training is a preemptive strike against potential threats. Also, Adversarial training can be used in various machine learning models like neural networks, support vector machines, or decision trees.
Deep Adversarial Metric Learning
In the pursuit of enhanced robustness, deep adversarial metric learning emerges as a sophisticated tool. Deep adversarial metric learning involves teaching a model to distinguish between real and deceptive examples by learning a distance metric. DAML improves deep metric learning by creating tricky synthetic samples challenging the learned metric. Adding these synthetic samples to the training set helps the algorithm measure distances between samples more accurately. For instance, measuring similarity or dissimilarity between pairs or triplets.
Defensive distillation
It involves training two models: a teacher and a student. It involves training a teacher model normally and a student model using softer probabilities from the teacher’s output. This method reduces a model’s vulnerability to adversarial changes by simplifying it. Moreover, this not only enhances the model’s resistance to adversarial influences but also makes it more efficient to understand. For example, a model can be distilled from a larger or more complex model to make it more smooth or linear.
Privacy-preserving machine learning
It is an approach aimed at safeguarding the confidentiality of data and models against potential exploration or exploitation attacks. Additionally, PPML models may employ encryption, anonymization, or differential privacy methods to hinder or restrict the unauthorized disclosure of information. For instance, adversarial learning can create a task-relevant representation that makes it challenging to reconstruct the original input.
Road Ahead
Looking ahead, the road to adversarial robustness for machine learning involves continuous exploration of new techniques to counter evolving threats. Researchers are likely to delve deeper into adversarial training, metric learning, and privacy-preserving methods. As ML becomes more integrated into critical domains such as healthcare and cybersecurity, fortifying models against attacks becomes increasingly essential. So, this dynamic field continues to be a focal point for innovation and development.
In conclusion, the journey towards adversarial robustness for machine learning invites ongoing exploration and innovation. Moreover, navigating the intricate landscape of adversarial challenges underscores the importance of continuous research and adaptation. Also, embracing this holistic approach ensures the robustness of machine learning models. Furthermore, it also facilitates the ongoing evolution of effective defense mechanisms in our dynamic technological landscape. Embracing this dynamic journey ensures a collective stride toward a safer and more robust technological frontier. So, join us in shaping the future resilience of ML, where shared insights contribute to the enhancement of security measures.

