What are Memecoins? An AI Agent Creates a Memecoin

Cryptocurrency constantly evolves, introducing fresh and exciting projects daily. A standout trend capturing attention is the rise of memecoins. These tokens thrive not on utility but on viral memes, strong communities, and internet culture’s dynamic influence. Today, we will explore what are meme coins and their rise in the crypto world. Additionally, we will examine […]
Robot Butterfly – Lab-grown brain cells move a Virtual Butterfly
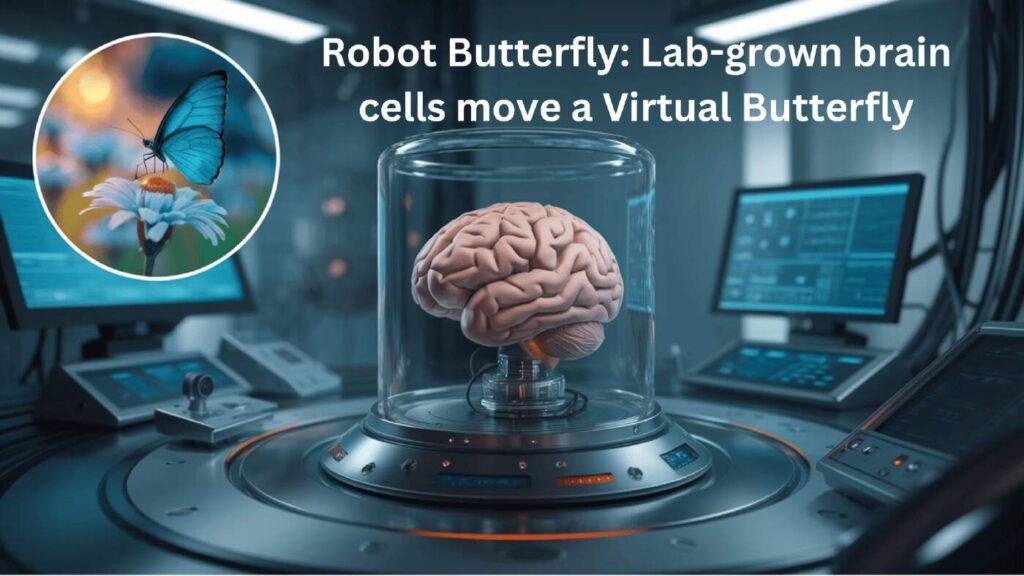
In a remarkable blend of cutting-edge neuroscience and robotics, scientists have successfully demonstrated a robot butterfly driven by lab-grown human brain cells. This extraordinary experiment opens up new possibilities for understanding how biological systems can control machines in virtual environments. Scientists grew human brain cells in a lab to guide a virtual butterfly in a […]
Digital Scent Technology

Our way of experiencing the world is being transformed by constantly evolving technology. A fascinating breakthrough, digital scent technology, could soon allow us to smell things through our devices. Imagine browsing a restaurant menu online and immediately catching the aromas of the food. Additionally, consider watching a movie where you can breathe fresh mountain air […]
Ultrasound AI: Revolutionizing Diagnostic Imaging

In recent years, AI systems have put professional ultrasound testers out of work by autonomously interpreting every second they capture. AI Ultrasound Imaging Systems seem destined for an upgrade to Artificial Intelligence. The incorporation of artificial intelligence (AI) into ultrasound imaging is beneficial for workstation-skilled image diagnosis systems and nurses as it enhances accuracy, efficiency, […]
Meta Quest 3s: Elevating the VR Experience

Virtual reality wonderfully shines on the fast lap of the modern technological environment and gets crowned with Meta in its top position. This most-awaited Meta Quest 3s VR headset will revolutionize how we experience virtual reality. With the latest technology, elegant design, and an immersive user interface, it is ready for widespread use. This innovation […]
Quest 3 Games

The Meta Quest 3 has debuted with a variety of thrilling new features and games. The release represents a significant advancement in VR technology. As the latest addition to Meta’s lineup, it offers major upgrades for immersive gaming. Therefore, we will compare the Quest 3 games to earlier versions. So, this article assesses whether the […]
CHIEF AI Model Predicts Cancer Diagnosis and Prognosis

Medical AI research is rapidly revolutionizing healthcare. One of the most impacted areas is cancer diagnosis and prognosis, where AI advancements are driving significant improvements. A new AI Model CHIEF to this revolution is a clinical histopathology imaging evaluation foundation capable of analyzing various tumor subtypes. This model is predicted to be a cornerstone of […]
Network Fabric: The Backbone of Modern Connectivity

In today’s digital landscape, businesses need smooth and efficient communication between their devices, systems, and data centers to succeed. A crucial factor in making this possible is a well-structured network fabric. This technology serves as the foundation that enables servers, storage devices, and systems to connect and communicate effectively. But what precisely is it, and […]
Neural Interface by Meta for Next-Gen Orion AR Glasses

In the ever-evolving world of meta wearables, Meta has now taken a monumental leap forward with its development. Moreover, they have created cutting-edge neural technology for their next-generation Orion AR glasses, further enhancing user experiences. This breakthrough is a key step in blending neuromodulation technology at the neural interface, enhancing human-computer interaction. These advancements position […]
ChatLLM Abacus AI

In today’s digital world, AI is changing industries, and ChatLLM by Abacus AI is an impressive language model. With its powerful features and user-friendly design, ChatLLM is ready to transform conversational AI for many uses. Additionally, as companies seek more efficient ways to enhance communication, ChatLLM Abacus AI offers a smart, powerful solution for engaging […]

